Partial, or masked, passwords is an authentication scheme where you’re asked to select or enter only specific characters from your password at a login screen – eg the 3rd, 5th and 7th characters:
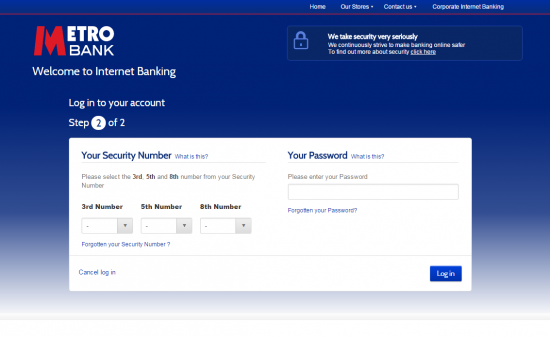
This got me thinking – normally passwords are stored on the server in an irreversible hashed format (there are many schemes, like bcrypt) which protects you in case the passwords are all dumped out in an attack. But in the case of partial passwords, is there a scheme that still preserves this protection? It seemed unlikely – a hash cannot reveal individual characters of a password; all information is destroyed in the process of hashing if it is truly a one-way function.
https://twitter.com/alexlomas/status/990137408472670209
The whole password would need to be stored in a recoverable form for individual characters to be compared. Does this imply plain text storage somewhere though? Not necessarily: the whole password can be stored encrypted in, say, a HSM. These individual characters can be presented to this black box which gives a yes/no answer back. Does this increase the risk that decrypted passwords could be extracted? Yes, because HSMs are not invulnerable, and if you don’t use a HSM, you’d better hope you have an excellent cryptographer on staff, maybe one that knows about Shamir’s Secret Sharing.
OK, so, there are some risks with password storage, most of which we can avoid by properly hashing, but if we do store passwords with reversible encryption (or not at all) is the trade-off worth it?
The threat model would appear to be one of shoulder-surfing or keylogging. If I can observe you entering your banking password in full, I need only capture it once, but if I ask for only 3 characters at a time, it will take me longer. But how much longer?
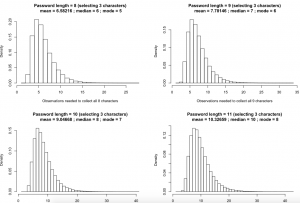
My lovely husband has written me some R to simulate this and you can have a tweak of some of the parameters below, but basically for an 8 character password with 3 characters asked for at random it takes about 6 times for an attacker to observe you before they have the full password.
Poorly implemented partial password schemes have additional flaws:
- By reducing a long password down to three choices, I’ve suddenly made it a lot easier to guess. An eight character alphanumeric password with mixed case gives 2^14 combinations, but many partial password schemes ignore case (it’s hard to scroll down that far for customers) so this is only 36^3 (~46,000) combinations which is quickly and trivially run through.
As a result, partial password schemes must be paired with a strong lockout system. - If the partial password selection is chosen at random at each refresh of the page, I can simply keep on asking for another sample until I get the ones I know.
Schemes must remember the required set for that “session” until the user successfully logs in and the selection is changed to another.
But in practice, many types of banking malware will simply modify the look of your bank’s login page in the browser to change the field to ask for the full password, send that to the crooks, who can then complete the “legitimate” three-out-of-eight challenge anyway.
All of this also actively discriminates against users of password managers – browser plugins that generate, store, and autofill long and random passwords for each site. If I have a 20 character password, I’m going to need to view it in plain text then manually count through each letter, number and interrobang to complete the challenge, thus displaying it for all to see and defeating the objective anyway. Password managers are actively encouraged by any sane and sensible security professional.
Once upon a time when keylogging and screenlogging malware was naïve this might have been a valid defensive measure, but the bad people quickly adapt and this is now an out of date and potentially risky approach to handling passwords.
What can we do then? Multi-factor authentication.
 I recently clicked over enough time elapsed (after deductions for my
I recently clicked over enough time elapsed (after deductions for my  I passed my
I passed my